
In our last update, we outlined the attributes of a threat management approach (Prevention, Detection, Containment, and Removal), and briefly discussed the potential weak areas (People, Processes, and Technology).
Today, we want to introduce an approach based on Prevention.
Common endpoint protection solutions are typically focused on 1.) threat detection, 2.) threat containment, and 3.) threat removal.
A critical component that these solutions don’t address is the prevention of vulnerabilities. Malware and Ransomware typically spread via weaknesses in software products (for example: web browsers, document creation tools, etc.) These weaknesses are called “Exploits” and allow the bad guys to execute their own program code on the vulnerable machine. Getting "infected" by such malware does not require any user’s mistakes! (besides opening a specific website or .pdf file which are both typically considered “harmless” and may even come from a trusted person/company).
Most software vendors actively monitor their products for ‘exploits’, and provide fixes in the form of software patches within a reasonable time frame after becoming aware a vulnerability exists.
Once a patch has been released, it is up to the end user or the IT department to ensure that these patches are being applied to all servers, desktops, and mobile devices in a timely manner.
Monitoring all software vendors for product patches and updates (including the operating systems of course) is a complex and time-consuming task. In addition to that, in many organizations, end users have products installed that the IT department does not know about, thus making a reliable patch management almost impossible.
Application of patches to all systems in a company in a pro-active, timely manner is the key to vulnerability prevention. With all systems patched from an operating system and application perspective, the risk of being a victim of a malware / ransomware attack is significantly reduced.
Because of the complexity and the manual nature of patch management, many companies are finding it difficult to stay current across all devices, potentially exposing their organizations to malware and ransomware attacks.

We would like to introduce you to an endpoint protection and management solution that removes the complexity by focusing on automation. Some of the key attributes of this offering include:
- Visibility to all systems in the enterprise
- Automated (or manual) application of patches to all systems in the enterprise
- Vulnerability analysis and reporting across all systems in the enterprise
- Compliance / Regulatory Analysis and Reporting
- Agent Based – Provides management for endpoints / systems that are remotely distributed
- Cloud Based
Real-time Visibility and Control
The solution provides a dashboard to easily view the security posture of all systems / endpoints in the enterprise. This allows real-time visibility into endpoint systems, including vulnerabilities, missing patches, processes, services, file information, security events, network connections, installed software, devices, privileged user accesses and rights.
Endpoint Risk Prevention
Our solution takes a “prevention” approach to endpoint security. This solution detects and fixes endpoint vulnerabilities and mis-configurations before exploits occur. Endpoints are automatically patched and hardened, simplifying the entire endpoint security process.
Threat Detection and Response
This software detects threats and includes remediation measures to instantaneously contain or block an attack. Threat Intelligence Cyber Feeds automatically detect Indicators of Compromise in seconds.
Regulatory Compliance
Daily checks ensure all endpoints meet regulatory compliance benchmarks. PCI, HIPAA, ISO 27001 and your internal organization standards are checked. Detected configuration discrepancies are then automatically fixed and documented for future reference.
Pricing
The pricing for this offering is provided in the table below. We believe we are offering a best of breed solution, that is affordable, easy to implement, will make a real difference in securing your company’s data and intellectual property, as well as simplify the day-to-day life of the IT administrator!
Here the pricing overview, there is a minimum of 50 endpoint licenses.
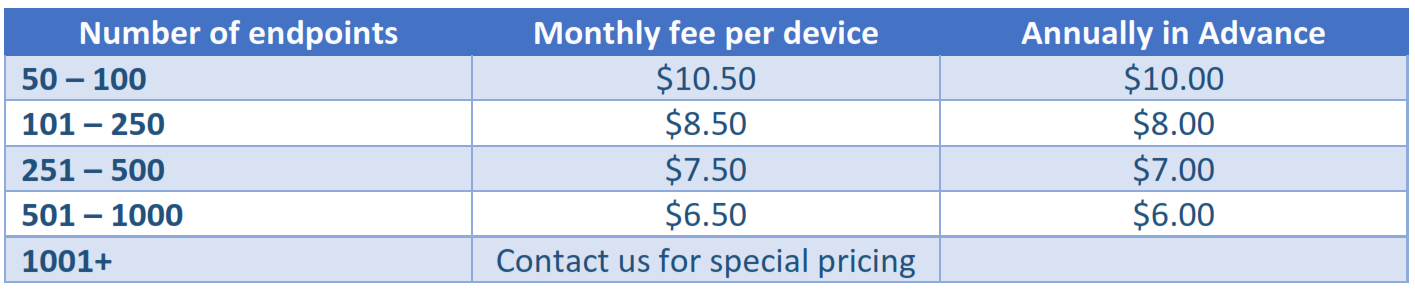
For an additional fee per endpoint, we also offer the complete management of the application, patch management for all your endpoints (including servers) and regular reporting on vulnerabilities and technical endpoint compliance. If you are interested in taking this task off your / your IT administrator’s plate, let us know and we will set up a call or meeting to discuss details and pricing options.
We hope that this information was helpful and gave you some thoughts around securing the IP and data of your organization. Of course, we would love you to reach out to us in case there is any area we can help with – either developing a security roadmap, finding the right technical solutions for your specific scenario or even with the definition and implementation of new processes.
Please feel free to reach out to either of us at any time for a discussion or to set up a meeting!




